Why This Topic Matters
Role-Based Access Control (RBAC) is one of those things that looks easy—
until your backend starts growing.
Most backend systems begin with:
Admin
User
And then reality hits.
Suddenly you need:
Multiple admin levels
Feature-based access
Permissions that vary by organization
Exceptions without breaking security
This is where poor RBAC design silently kills scalability.
This article explains how RBAC should be designed in large backend systems, independent of framework — whether you’re using Django, Node.js, or NestJS.
What Breaks First in Naive RBAC Implementations
Before designing anything, it’s important to understand why RBAC fails.
❌ Common RBAC Mistakes
Checking roles directly in controllers
Hardcoding conditions like
if user.is_adminMixing access rules with business logic
Adding “temporary exceptions” that become permanent
These approaches work for small apps —
but collapse as soon as teams, features, and data grow.
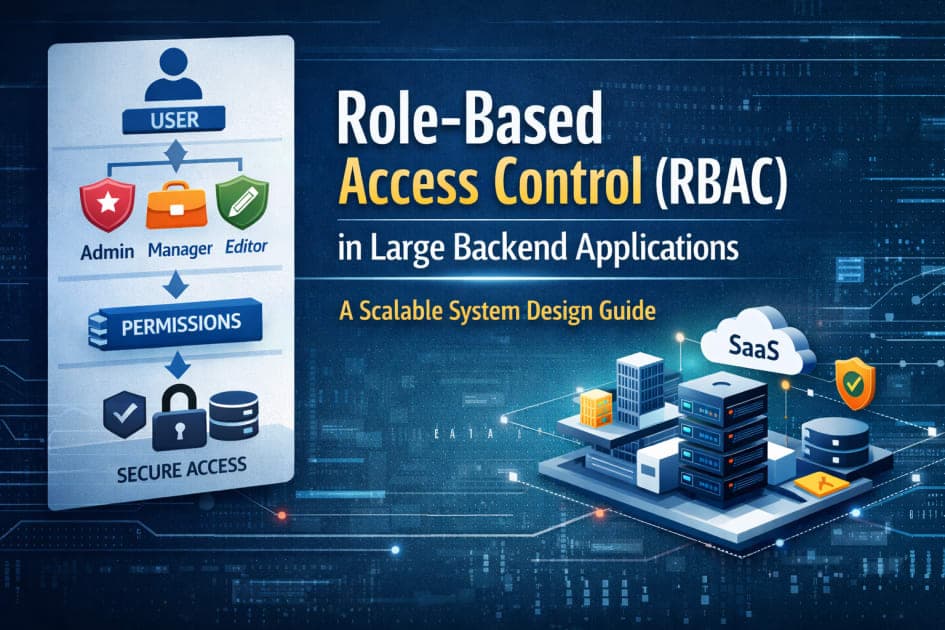
Core Design Principle: Roles ≠ Permissions
This is the single most important concept.
Roles should group permissions — not replace them.
❌ Wrong Mental Model
User → Role → Access✅ Correct Mental Model
User → Role → Permissions → AccessRoles are labels.
Permissions are rules.
If your backend checks roles directly, it will not scale.
High-Level RBAC Architecture (Diagram)
Here’s the structure used in large systems:
[ User ]
↓
[ Role(s) ]
↓
[ Permission(s) ]
↓
[ Protected Action / Resource ]
And optionally (very important in SaaS):
[ Context ]
(organization / tenant / project)This separation keeps access logic:
Predictable
Testable
Extendable
Designing Permission-First Access Control
Instead of writing logic like:
if user.role == "admin":
allow()
Large systems ask:
if user.has_permission("manage_users"):
allow()Why this works better:
Permissions can be reused
Roles can evolve
Access rules stay consistent
New roles don’t require code rewrites
Example: Permission-Based Check (Framework-Agnostic)
Conceptual Pseudocode
function canAccess(user, permission, context):
return permission in user.permissions_for(context)This logic works in:
Django services
Express middleware
NestJS guards
The framework changes — the design does not.
Where RBAC Logic Should Live (Very Important)
RBAC should NOT live in:
Controllers
Views
Routes
Serializers
Why?
Because duplication leads to inconsistency.
✅ Correct Placement
Controllers → Services → Access Control LayerRBAC belongs to a dedicated access layer:
Permission services
Policy classes
Guards / middleware
This keeps security centralized.
RBAC with Context (Multi-Tenant Systems)
Large systems are rarely single-context.
Example:
A user is an admin in School A
Same user is a viewer in School B
Context-Aware RBAC Diagram
User
↓
Role
↓
Permission
↓
Context (Tenant / Org / Project)
↓
ActionThis is mandatory for:
SaaS platforms
ERP systems
Enterprise dashboards
How This Translates Across Frameworks
Django
Permission tables or services
Middleware or service-level checks
Avoid
is_staff/is_superusereverywhere
Node.js (Express / Fastify)
Middleware-based permission validation
Centralized policy functions
No role checks inside routes
NestJS
Guards + decorators
Policy-based access control
Clean separation of concerns
The thinking remains identical.
Scaling RBAC Without Rewriting Code
A good RBAC system allows:
Adding new roles without code changes
Changing permissions without redeploys
Feature-based access toggling
Clear audit trails
If adding a role requires touching many files,
RBAC is already broken.
RBAC vs Business Logic (Keep Them Separate)
Access control answers:
“Can this user do this?”
Business logic answers:
“What happens when they do?”
Mixing them:
Increases bugs
Breaks tests
Confuses teams
Separation:
Access Layer → Business Logic → Data LayerThis is non-negotiable in large systems.
Final Takeaway
RBAC is not a feature.
It’s backend infrastructure.
Bad RBAC:
Slows development
Creates security holes
Becomes impossible to maintain
Good RBAC:
Scales quietly
Makes systems safer
Lets teams move faster
This design approach is used in large, production-grade backend systems, regardless of whether the stack is Django, Node.js, or NestJS.
About the author
Slow, bloated web apps lose users and rankings.
I build fast, scalable, SEO-ready web applications using Next.js, MERN, and Django.
My focus is clean architecture, performance, and long-term stability.
I don’t ship demos — I ship production-ready systems.